(To support my writing, I may use affiliate links in this post. Rest assured, they don’t affect my reviews.)

If you’re looking to start a career in cybersecurity with no prior knowledge or experience, I’ve got an excellent certification program to recommend—the IBM Cybersecurity Analyst Professional Certificate, available on Coursera.
Earlier, I shared my review of the Google Cybersecurity Certificate, which is also a good option for beginners. However, in my opinion, it lacks the depth offered by the IBM program. If you’re interested in a side-by-side comparison of both, just let me know!
Now, let’s talk about the IBM Cybersecurity Analyst course…
This program has 4.7 star ratings by 13,376 students (reviewed). It is not only beginner-friendly but also designed to prepare you for entry-level roles in the cybersecurity field—such as Cybersecurity Analyst, SOC Analyst, Security Consultant, Incident Responder, and more.
The best part? It doesn’t cost thousands of dollars like traditional bootcamps, and you can learn entirely at your own pace.
Sounds interesting?
In this quick review, we’ll explore whether the IBM Cybersecurity Analyst course is worth your time and investment in 2025.
Introduction to IBM Cybersecurity Analyst Certification:
Created by senior practitioners at IBM, this certification program is an 14-course series designed to help you learn cybersecurity in 5 to 6 months—no prior knowledge or experience required.
The program includes recorded video lessons, reading materials, quizzes, assignments, and more. What stands out most is its emphasis on real-world projects and hands-on learning using the same cybersecurity tools that professionals use daily.
Throughout the program, you’ll learn from multiple instructors—each an expert in their field and currently working at IBM. They bring valuable insights from different areas of the cybersecurity industry.
By completing this program, you’ll gain a solid understanding of key cybersecurity skills, including threat detection, incident response, risk management, penetration testing, vulnerability assessment, and security analysis.
How Much Does IBM Cybersecurity Analyst Certificate Cost?
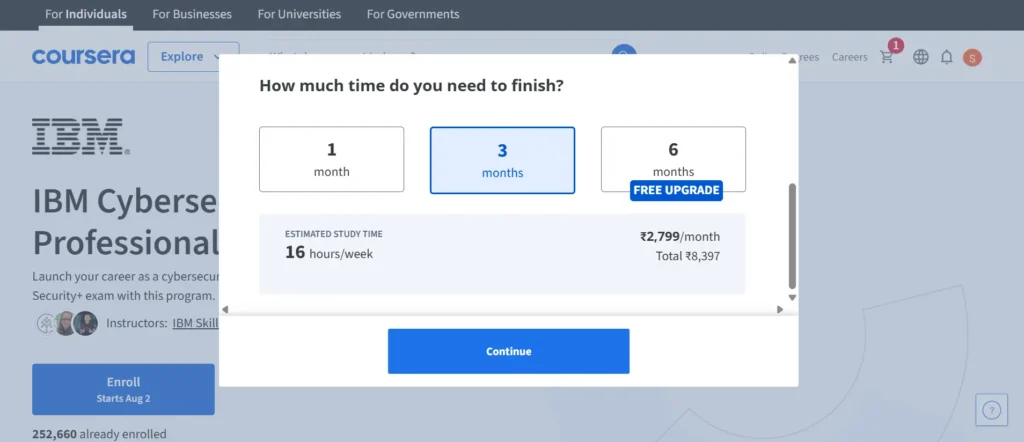
The IBM Cybersecurity Analyst Certificate costs $49 per month on Coursera and comes with a 7-day free trial.
The total cost depends on how long you take to complete it and your location—for example, around $147 for 3 months or $297 for 6 months.
In India, the estimated cost is ₹8,397 for 3 months and ₹12,596 for 6 months (with 6-months free Coursera Plus access).
Most learners finish the program within 6 months by studying 10–12 hours per week. Thanks to Coursera’s flexible subscription model, you can learn at your own pace—according to your schedule and budget.
Although the same program is available on edX, Coursera tends to be slightly more affordable for this certification.
What’s Included in This Program: Course Curriculum
The IBM Cybersecurity Analyst Certification is designed to help you develop essential skills in cybersecurity. It includes 14-series courses, each focusing on a specific area of cybersecurity, such as network security, penetration testing, and more.
While you can take these courses in any order, following them in sequence will help you learn and develop your skills more effectively.
The courses are taught by experts from IBM and its partner network, who bring real-world experience to the classroom.
Let’s take a closer look at what you’ll learn in each course…
1. Introduction to Cybersecurity Careers
If you’re completely new to cybersecurity, this course gives you a solid overview of different careers in cybersecurity, helping you understand the roles, responsibilities, and how to move from beginner to advanced levels.
You’ll learn how IT fundamentals, technical know-how, and soft skills connect with specific job roles at each stage. It also introduces you to key certifications like Security+, A+, CISSP, and CEH—what they cover and who they’re for.
By the end, you’ll have a clear idea of which cybersecurity path suits you best and how to start preparing for it with the right skills and credentials.
2. Introduction to Cybersecurity Essentials
This course covers the basics of keeping data safe and secure. You’ll learn why data integrity and confidentiality matter, and how regular software updates and patches play a key role in protection.
It also walks you through best practices for authentication, encryption, and securing your devices.
Plus, you’ll get familiar with common cybersecurity threats like malware, data breaches, social engineering, and other attack methods—so you can understand how attacks happen and how to defend against them.
3. Introduction to Cybersecurity Tools & Cyber Attacks
This course explores the cybersecurity case studies. ! You’ll explore the history of cyber attacks and key concepts like the CIA triad (Confidentiality, Integrity, and Availability).
You’ll also learn about essential tools such as firewalls, antivirus software, and penetration testing. It’s perfect for those new to cybersecurity or looking to improve their online security.
4. Operating Systems: Overview, Administration, and Security
This course builds your foundational knowledge of operating systems—essential for anyone starting a career in cybersecurity or IT support.
You’ll learn how to navigate the key features of Windows, Linux, and macOS, and understand what makes each system unique. It also covers how to manage user accounts and set permissions effectively.
On top of that, you’ll get introduced to core cloud computing concepts like virtualization and containerization, which are becoming increasingly important in today’s tech landscape.
5. Computer Networks and Network Security
This course teaches the in-demand skills needed to secure computer networks and endpoint devices from threats and intrusions.
You’ll learn how to apply organizational policies using firewalls and rulesets to protect devices effectively. It also walks you through installing, configuring, and patching systems, as well as using cloud-based tools to detect, quarantine, and remove malware.
Plus, you’ll explore intrusion detection systems and learn how to recommend the right network hardware, security solutions, and monitoring tools to keep networks safe and running smoothly.
6. Database Essentials and Vulnerabilities
This course equips you with job-ready data management skills that employers look for—especially around protecting sensitive information. You’ll learn how to configure and manage database user profiles, set password policies, assign privileges, and define roles securely.
It also dives into identifying and mitigating injection vulnerabilities, including OS command and SQL injection attacks. Plus, you’ll explore how to design and implement robust auditing models to monitor database and application activity, making your systems more secure and compliant.
7. Cybersecurity Architecture
This course introduces you to the five core principles of cybersecurity along with the well-known CIA triad—Confidentiality, Integrity, and Availability. You’ll explore what a cybersecurity architect considers when building a secure enterprise solution.
It also breaks down key security domains like identity and access management (IAM), endpoint security, network security, application security, and data security.
By the end, you’ll be able to analyze a scenario and confidently recommend practical methods to strengthen network security.
8. Cybersecurity Compliance Framework, Standards & Regulations
This course dives into the fundamental concepts of cybersecurity, covering governance, risk management, compliance, AI ethics, and how audits are conducted.
You’ll get familiar with key cybersecurity laws and regulations—both national and international—and understand what they mean for organizations. It also explores important industry standards, with a focus on frameworks like COBIT and SOC reports.
By the end, you’ll know how to apply these standards and best practices to reduce risks, strengthen security, and maintain compliance through effective audit processes.
9. Penetration Testing, Threat Hunting, and Cryptography
This course focuses on in-demand skills like penetration testing and threat hunting—exactly what employers want to see on a resume. You’ll get hands-on experience using tools like OWASP ZAP and SNYK to simulate real-world attacks.
The course also teaches you how to create detailed penetration testing reports and leverage AI for advanced threat hunting and intelligence gathering. Additionally, you’ll dive into cryptography and cryptanalysis techniques such as encryption and hashing to protect data and maintain its integrity and confidentiality.
10. Incident Response and Digital Forensics
This course introduces you to the core principles and importance of incident response in cybersecurity. You’ll learn how to detect and analyze security incidents using industry-relevant techniques and tools.
It also covers methods for collecting and examining digital evidence, helping you understand how to handle data during and after an attack. By the end, you’ll be able to analyze forensic findings and create reports that support cybersecurity investigations and strengthen overall incident response efforts.
11. Cybersecurity Case Studies and Capstone Project
This capstone course offers hands-on experience with real cybersecurity case studies, helping you identify threats and assess vulnerabilities—great for interview prep.
You’ll apply forensic techniques and response frameworks to real-world breach scenarios, and gain skills in penetration testing and compliance analysis. You’ll also research real data breaches and learn how to analyze them to propose practical security improvements.
12. Cybersecurity Assessment: CompTIA Security+ & CYSA+
This course helps you get exam-ready for CompTIA Security+ and CySA+ with focused study tips and proven exam-day strategies. You’ll validate your knowledge through practice tests and timed mock exams, ensuring you’re confident and well-prepared.
It also breaks down the key domains covered in each exam and explains how they’re scored. Plus, you’ll understand the full certification process—from registration to test-day procedures—so there are no surprises.
13. Generative AI: Boost Your Cybersecurity Career
This course introduces the fundamentals of Generative AI and its growing role in cybersecurity. You’ll learn how to apply AI techniques to real-world scenarios like UBEA, threat intelligence, report summarization, and automated playbooks.
The course also explores how AI can defend against phishing, malware, and NLP-based attacks. You’ll study real-world case studies and learn how to mitigate risks and secure generative AI models, while identifying what makes successful implementations work.
14. Cybersecurity Job Search, Resume, and Interview Prep
This is the last course that helps you get job-ready by breaking down common cybersecurity roles, titles, responsibilities, and the skills needed—aligned with the NICE framework. You’ll learn how to build a strong resume, portfolio, cover letter, and elevator pitch, plus apply best practices to succeed in job interviews.
It also prepares you to answer both technical and behavioral interview questions confidently. Finally, you’ll learn what to do after the interview and get practical tips for negotiating your salary and setting yourself up for long-term success.
Can You Get A Job with IBM Cybersecurity Analyst Certificate?
Well, regarding this query, I’ve spoken with several graduates of the IBM Cybersecurity Analyst program on LinkedIn, Reddit, and other forum sites.
Based on their insights, the certificate alone might not be enough to land a job, as employers often look for practical, hands-on skills beyond the training. That said, the program does a good job of preparing you for entry-level roles like cybersecurity analyst, incident responder, or security engineer.
To improve your chances, it’s best to supplement the IBM certificate with hands-on projects, certifications like CompTIA Security+, and proven technical skills. This combination can make you a much stronger candidate in the field.
What I Like About IBM Cybersecurity Analyst Course:
- It includes all the course materials you need to learn about cybersecurity, even if you’re starting from zero. Good for beginners.
- You get valuable knowledge and skills to start a career in cybersecurity and apply for entry-level jobs like SOC, security analyst, etc.
- The exams are tough but really test how much you learned. Finishing them gives you a sense of achievement.
- After each section, there are quizzes to help reinforce the main concepts. Notes and resources help too.
- It’s a great intro to cybersecurity if it interests you. Easy to understand stuff and teaches you core skills.
Limitations of IBM Cybersecurity Analyst Course:
- Some instructors in the first courses are boring, they repeat things and make it boring and poor presentation.
- There are technical problems like grading systems not working right, questions that are written badly, and static noise in the videos.
- You don’t get feedback on exams and quizzes. And even if you take them again, your scores are different.
- For peer-reviewed assignments, there’s not enough checking and students might copy each other’s work.
Final Verdict: Is the IBM Cybersecurity Analyst Certificate Worth It?
From my personal experience—and based on feedback from others who’ve completed it—I found the IBM Cybersecurity Analyst program to be a solid option for anyone starting out in cybersecurity.
It starts from the basics and gradually builds the core skills needed for roles like cybersecurity analyst, SOC analyst, incident responder, or even a junior security engineer. You don’t need any prior experience, and the content feels beginner-friendly and practical.
That said, it’s not without flaws. Some learners reported things like average video quality, occasional glitches, and limited instructor feedback. But honestly, the overall value still outweighs these issues.
The final assessment really helps tie everything together and boosts your confidence for real-world scenarios.
Overall, I’d rate it 4.5 out of 5. If you’re just getting started, it’s a well-structured, skill-based program that actually prepares you for the job.
Now It’s Your Turn!
I hope you enjoyed this review and found it helpful in evaluating if this is the right cybersecurity program for you. Please let me know in the comments if you have any other questions about the IBM certification.
If you’ve decided to enroll in the program, I wish you the very best on your cybersecurity learning journey!
If you want to explore alternative cybersecurity programs, check out the FAQs below for recommendations on other highly-rated options for beginners. I’m happy to offer guidance on finding the perfect program to achieve your career goals.
FAQs:
IBM Cybersecurity Analyst Course vs. Google Cybersecurity Certificate – Which is best?
The IBM Cybersecurity Analyst Professional Certificate isn’t the only good option for beginners. The Google Cybersecurity Professional Certificate on Coursera is also beginner-friendly, affordable, and well-structured.
While the Google program is highly engaging and easier to follow, it may not go as deep into certain topics as the IBM course. IBM’s curriculum is more extensive and includes tougher assessments, which can better prepare you for real-world job roles. Both are solid programs.
If you’re looking for a more hands-on, in-depth experience, IBM might be the better fit. But if you’re just getting started and want something approachable, Google’s certificate is a great starting point.
What is the Avg. Salary of IBM Cybersecurity Analyst Professional Certificate Graduates?
As you know, the graduates of the IBM Cybersecurity Analyst Professional Certificate typically go into entry-level cybersecurity roles such as: Cybersecurity Analyst, SOC Analyst (Security Operations Center), Information Security Analyst, IT Security Specialist.
Average starting salary after completing the IBM Cybersecurity Analyst Certificate is around $65,000 to $75,000/year in the U.S., assuming it’s your entry point into the field. With some experience or additional certifications, this can rise quickly.
Read also: My Honest Review of IBM Data Science Professional Certificate (2026)

